0xl4ugh2024
0xl4ugh2024
I participated in the 0xl4ugh2024 I solved all forensics challenge,and this is my write-up for most forensics challenges
Gamer - 1
it’s disk so i opened it with MagnetAxiom
in the challenge he said that An employee downloaded an unauthorized app so we will look for browser history
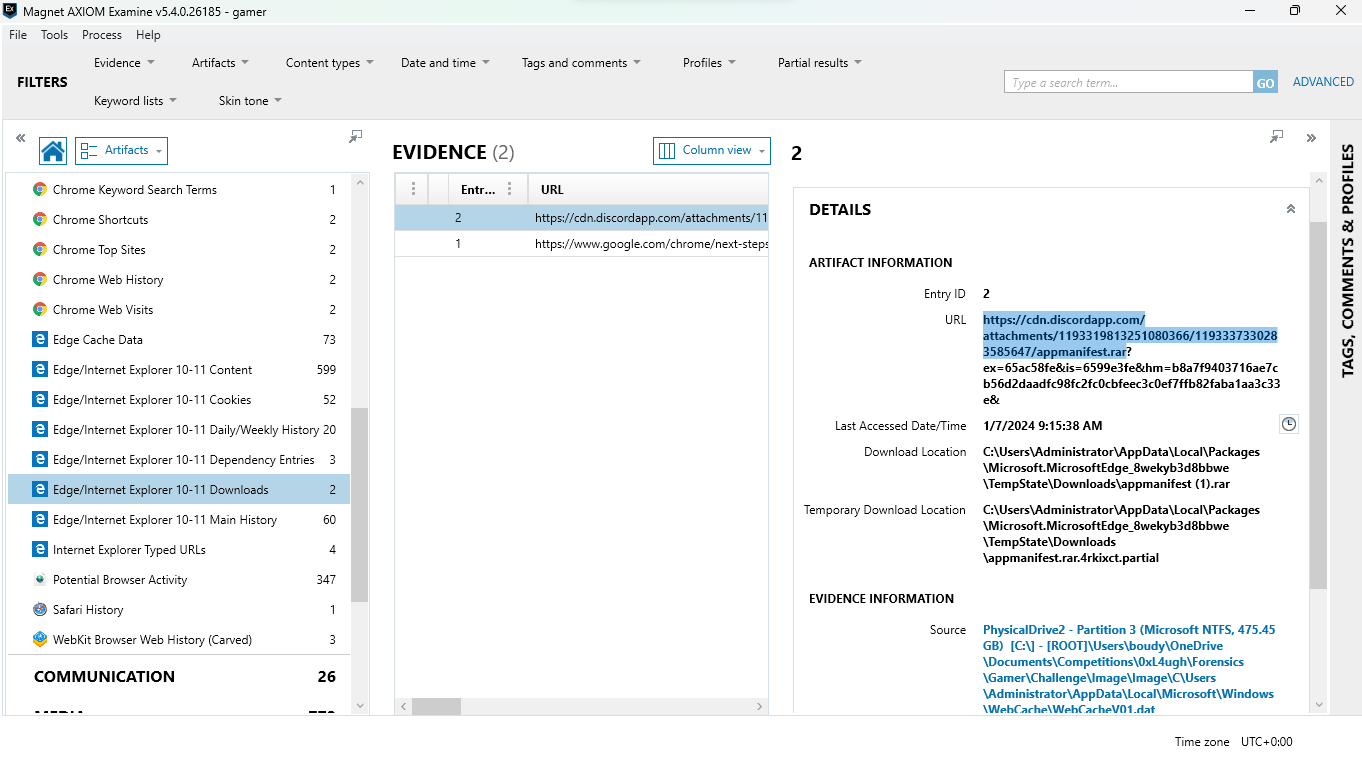
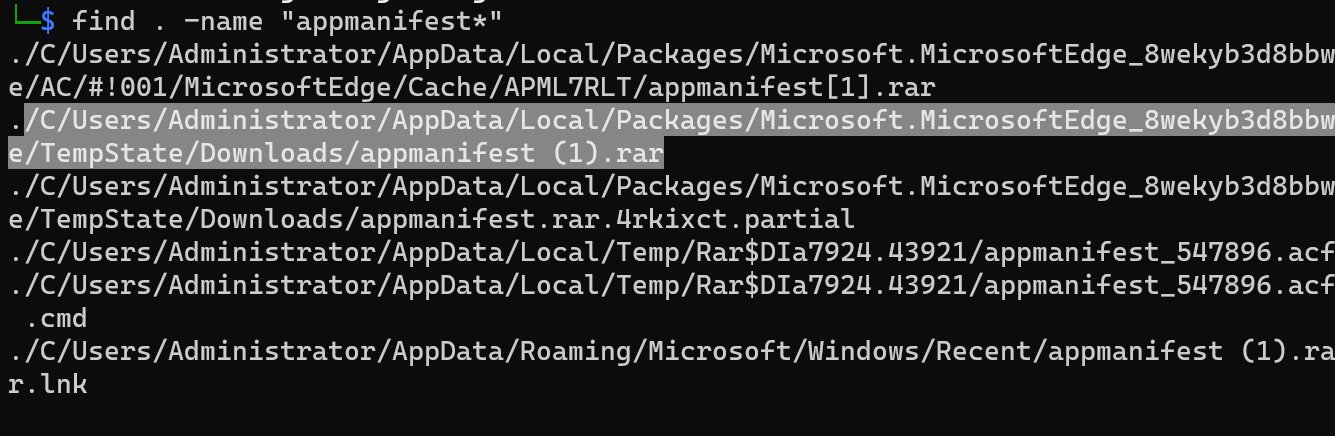
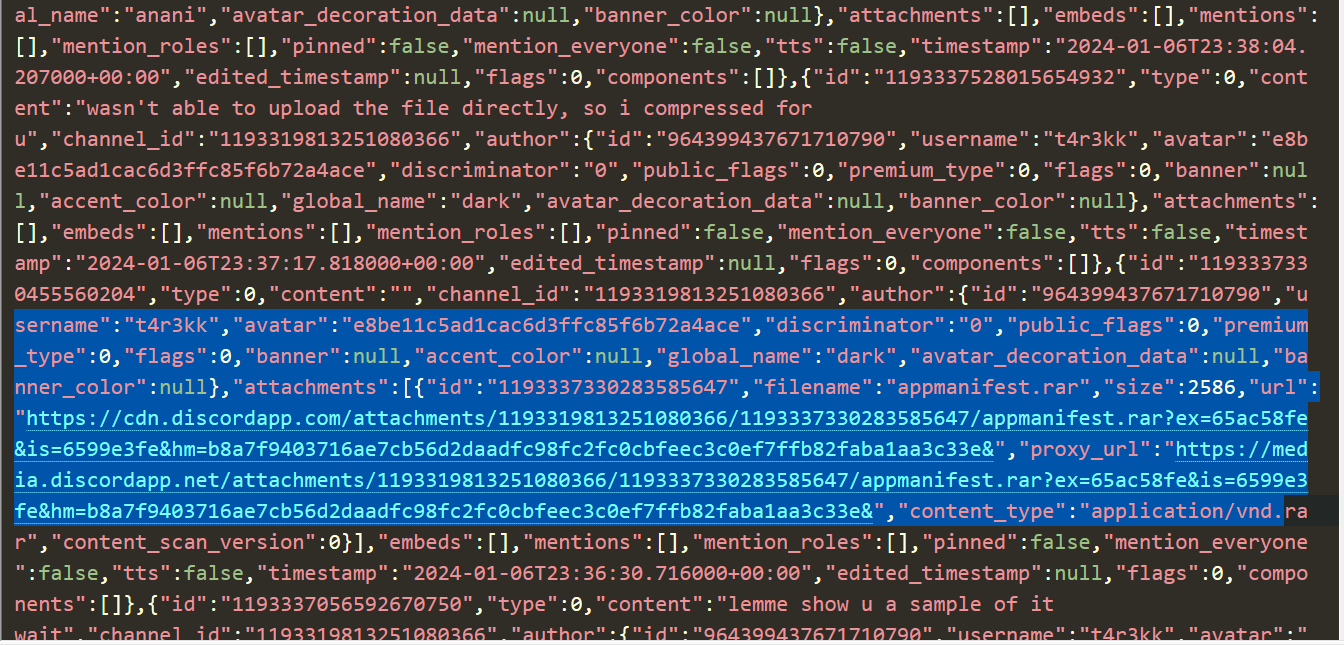
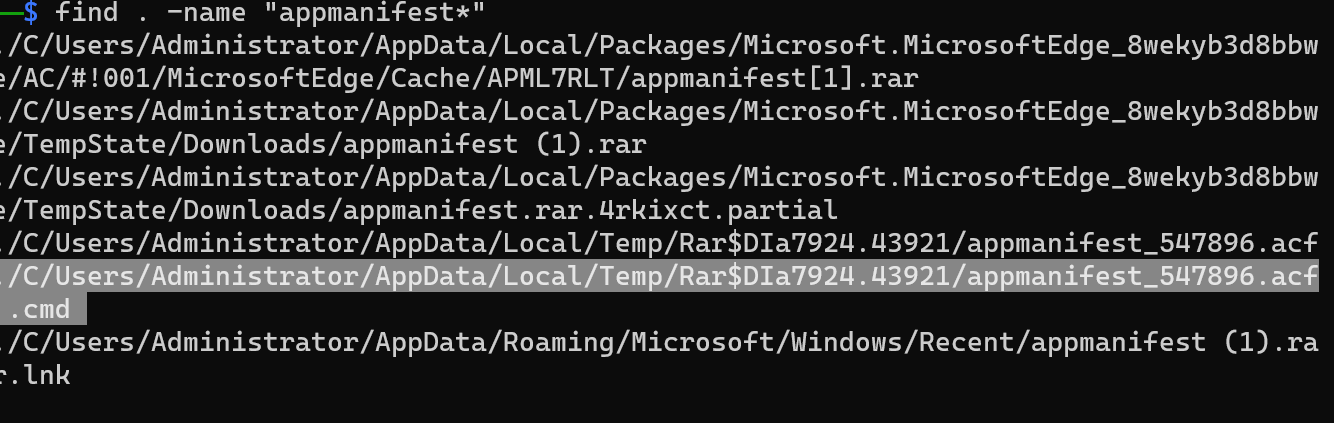
so we look we found that there is suspicous .rar file downloaded from disord we know that it’s name is appmanifest.rar so let’s search about it in disk find . -name "appmanifest*"
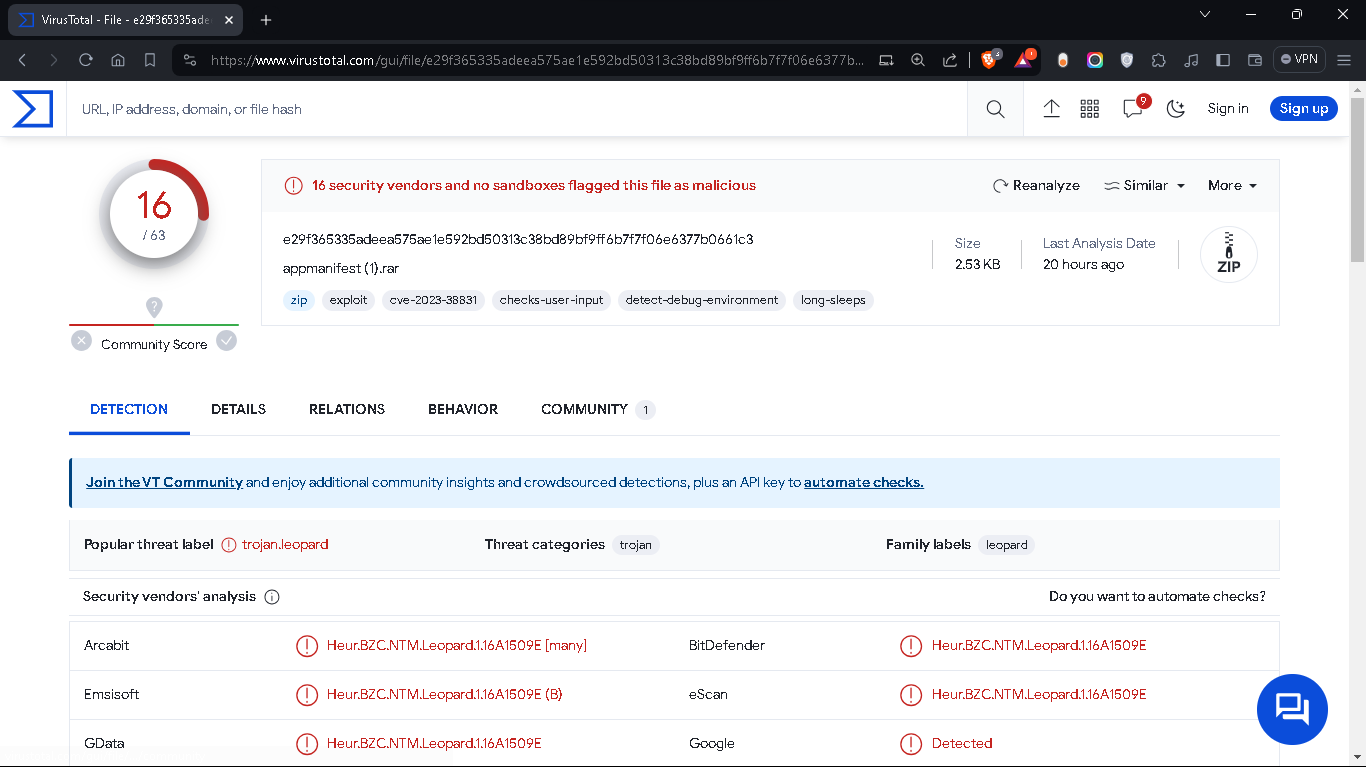
so we found it let’s calculate it’s hash sha256sum appmanifest (1).rar we found e29f365335adeea575ae1e592bd50313c38bd89bf9ff6b7f7f06e6377b0661c3 now upload it to virus total to see it’s have malware or not
so we know know that it’s malicious and we got cve of it cve-2023-38831 now we know that this is attacker sent it in discord and it have malware we will analyze it later
now we need to analyze discord cache file this link helped me so i downloaded this tool and i opened cache file in this program and extract all files by click ctr a and then press f4 and then i opened 50.json file
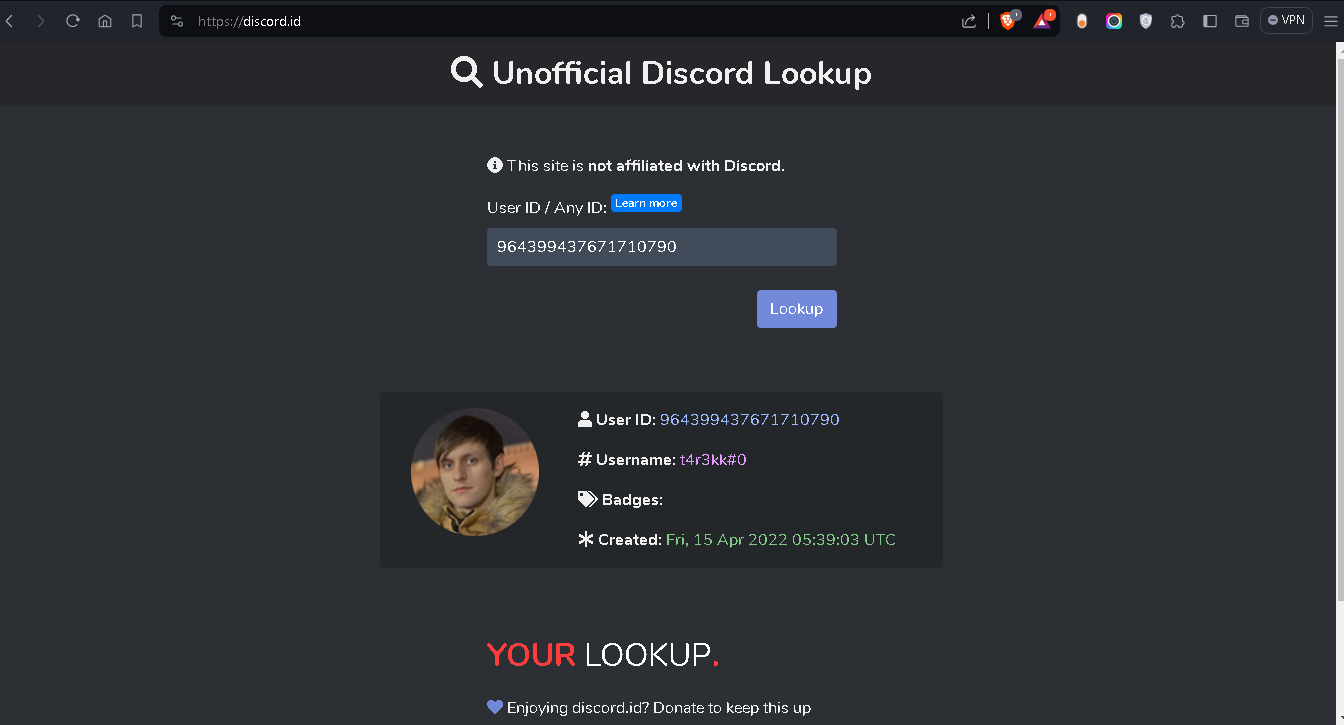
now we know that t4r3kk who sent the malicious .rar file to the victim we need to know create time for this user so we use this website and put id 964399437671710790
now we know creation date and id and i did some osint i got the real name of attacker
flag: 0xL4ugh{Discord_1.0.9028_964399437671710790_15-04-2022_05:39:03_IgorDekhtyarchuk}
Gamer - 2
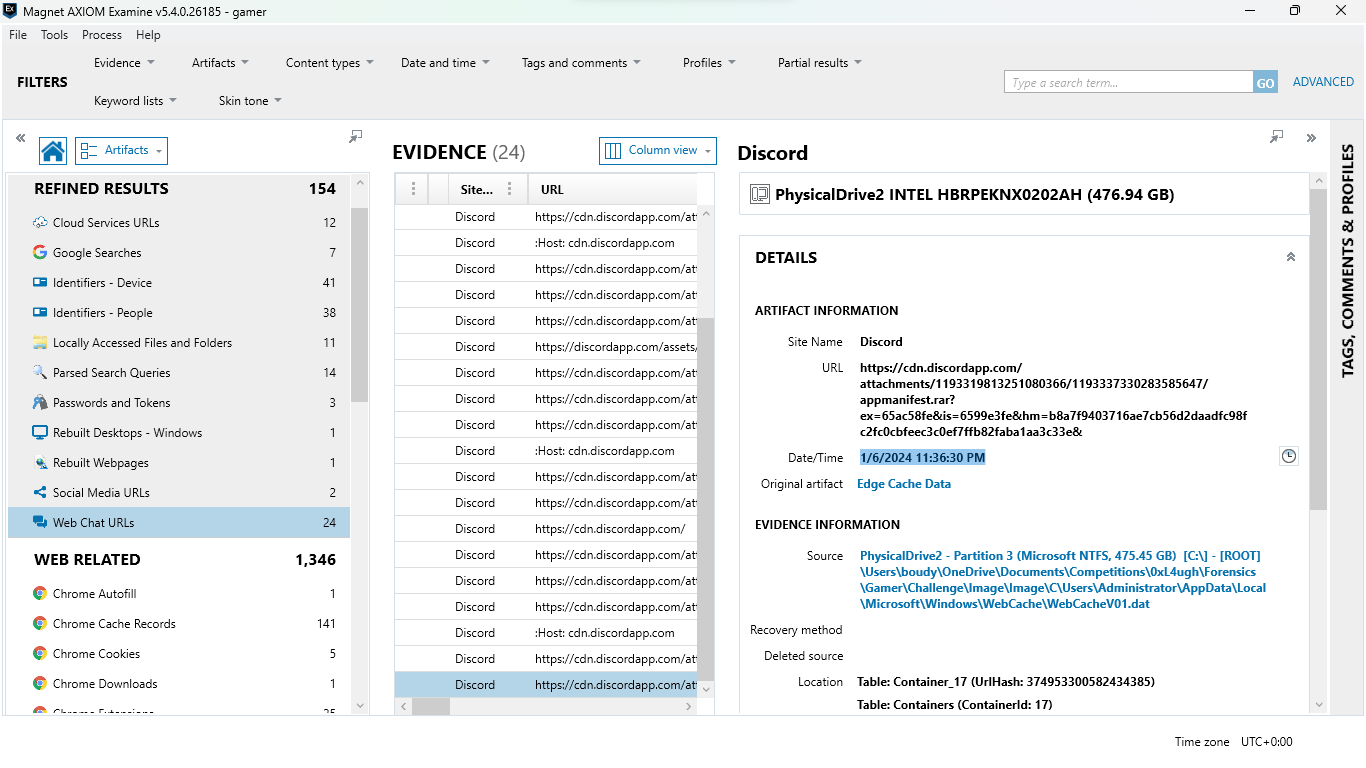
now here we know sha256 of file and we know the cve we got in first question so now we need to know when this is .rar is installed in the system
this is the first time the file is downloaded to system
and the first time it executed
now date_of_execution - date_of_downloading
flag: 0xL4ugh{e29f365335adeea575ae1e592bd50313c38bd89bf9ff6b7f7f06e6377b0661c3_09:39:44_CVE-2023-38831}
Gamer - 4
ok when we searched about malware with find . -name "appmanifest*" we found suspicious file
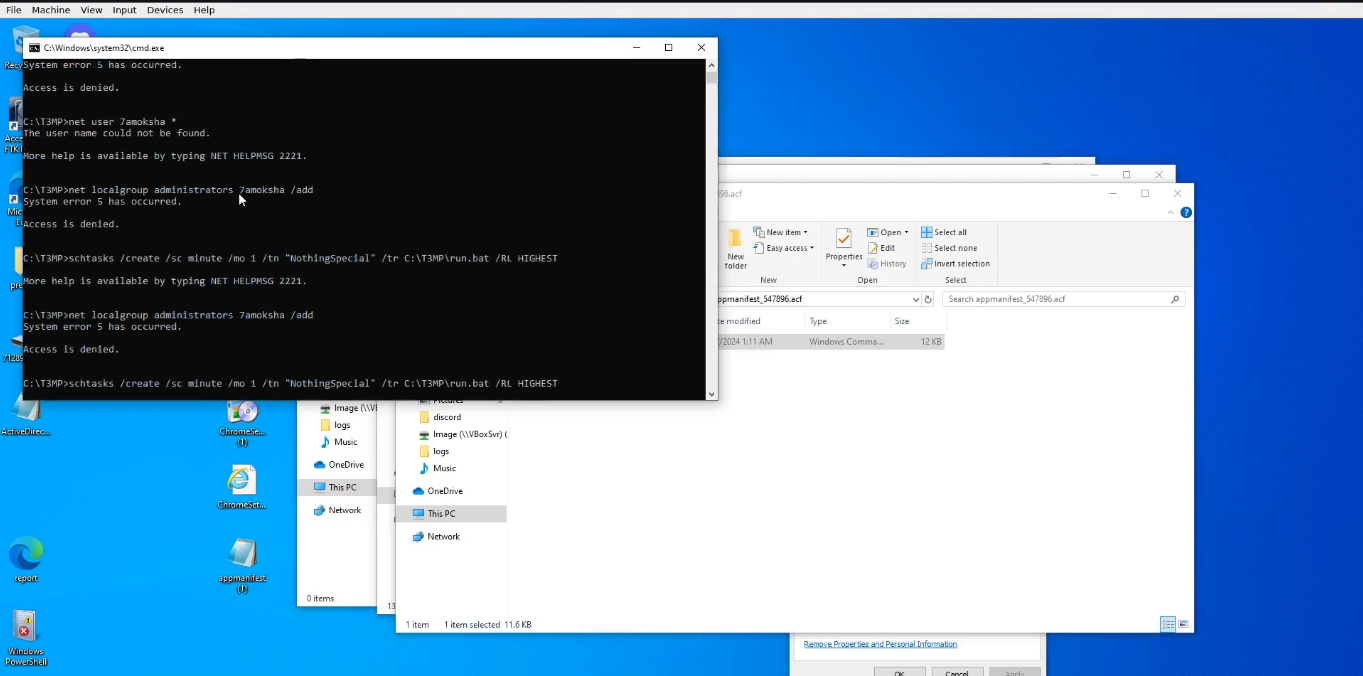
so i run this script in the virtual machine windows
so from there we got the command and file
flag: 0xL4ugh{NothingSpecial_C:\T3MP\run.bat}
This post is licensed under CC BY 4.0 by the author.